
In August 2018, the Internet Engineering Task Force (IETF) approved the 1.3 version of TLS, a more secure and more efficient version. It gives a specific response to vulnerabilities that have appeared in recent years. More so, TLS 1.3 promises reduced connection latency thanks to less round-trips and the 0-RTT option.
Here is all you need to know about one of the most important changes of the web at the moment. What are the differences with older versions? How is the TLS 1.3 version better than TLS 1.2? What does this actually mean for you and your users?
TLS 1.3 = better performance
TLS 1.3 is the promise of a secure, more efficient website, thanks to a limited number of exchanges between the server and the customer.
Indeed, the number of round-trips between the server and the client is a factor that may limit the performance of the protocol. The TLS 1.3 connection setup requires only one round-trip (versus two for TLS 1.2).
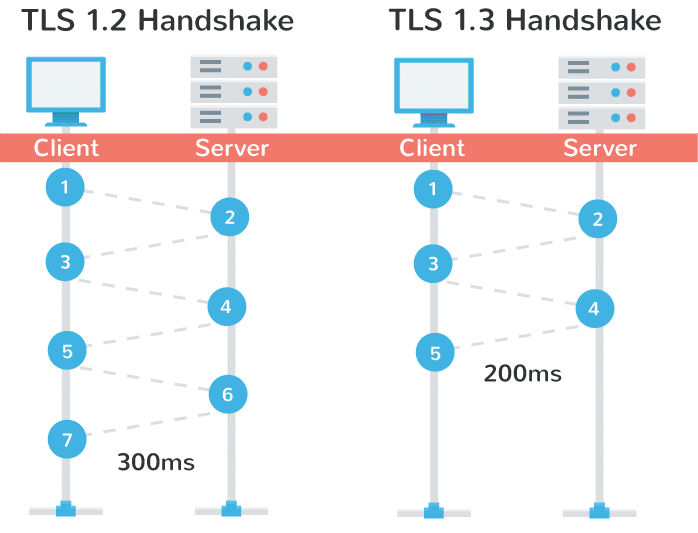
Source : Kinsta
0-RTT: what makes TLS 1.3 perform better
TLS 1.3 also includes an option called 0-RTT (zero round-trip) which allows you to go back to websites you have previously visited without renegotiating encryption.
Thus, during the very first connection of a client to the server, there is complete negotiation. The client keeps a cached message, Server Config (SCFG). All subsequent connections will use it to get derived keys and start exchanging data immediately.
The client may send data to the server on the first message to the server.
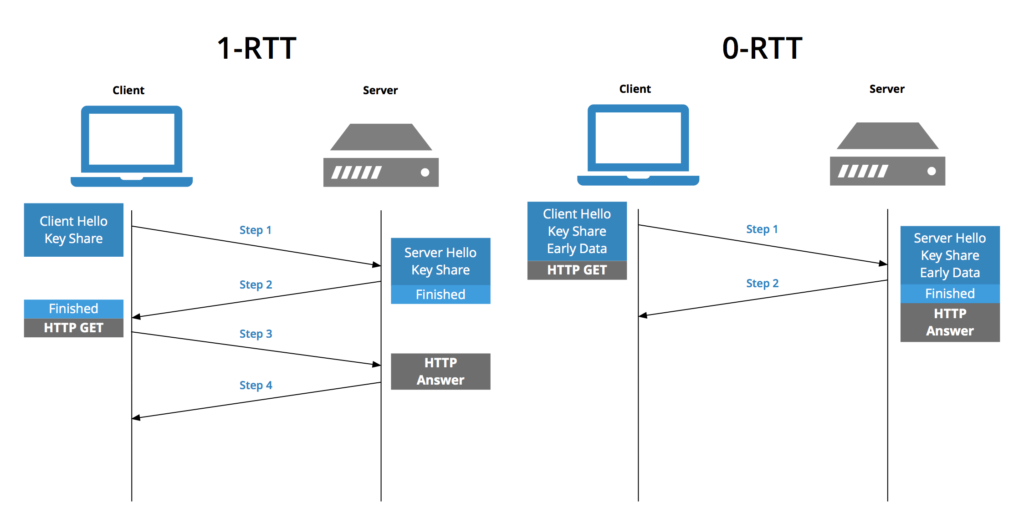
Source : Key CDN
Result: With TLS 1.3, secure web pages load faster!
Major security differences between TLS 1.2 and TLS 1.3
10 years ago, TLS 1.2 focused on cryptographic improvements, especially in hashing. In recent years, security breaches such as Crime, Drown, or Lucky 13 appeared. TLS 1.3 is a solution to the latter.
Alternatives and more limited primitives
One of the main weaknesses of TLS 1.2 is that it uses a fairly large variety of cryptographic algorithms. Amongst them, vulnerable primitives contribute to weak TLS configurations. Too often misconfigured, because of this variety, TLS 1.2 leaves websites vulnerable to security breaches.
TLS 1.3 abandons the obsolete and unsecured features of TLS 1.2 (such as SHA-1, RC4, DES, 3DES, AES-CBC, MD5) for more secure alternatives (such as ChaCha20, Poly1305, Ed25519, x448 and x25519). The choice of primitives is now more limited and makes TLS configuration easier.
User privacy better protected
In previous versions of TLS, the handshake ran in clear, which could result in information leakage (including client and server identities).
Furthermore, as Mozilla explains, "many network middleboxes (intermediate systems for web traffic) used this information to enforce network policies and failed if the information wasn't where they expected it. This could break the protocol when new features were introduced. TLS 1.3 encrypts most of the handshake, which provides better privacy and, gives us more freedom to evolve the protocol in the future. "
Where are we with the implementation of TLS 1.3?
TLS 1.2 is currently the most widely used version of the protocol by websites (around 80 % of websites). TLS 1.3 represents 89% of the traffic on our platform in 2020. All browsers have already implemented the TLS 1.3 specification, Google and Facebook also run it on their servers..
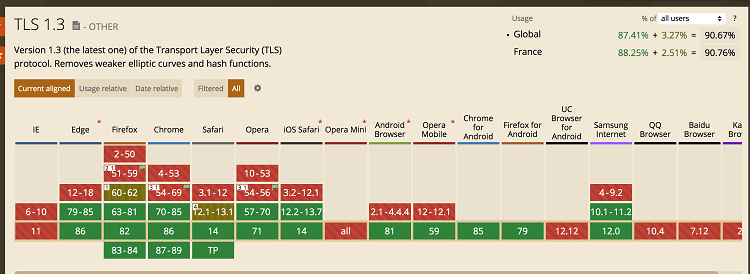
TLS 1.3 support by browsers
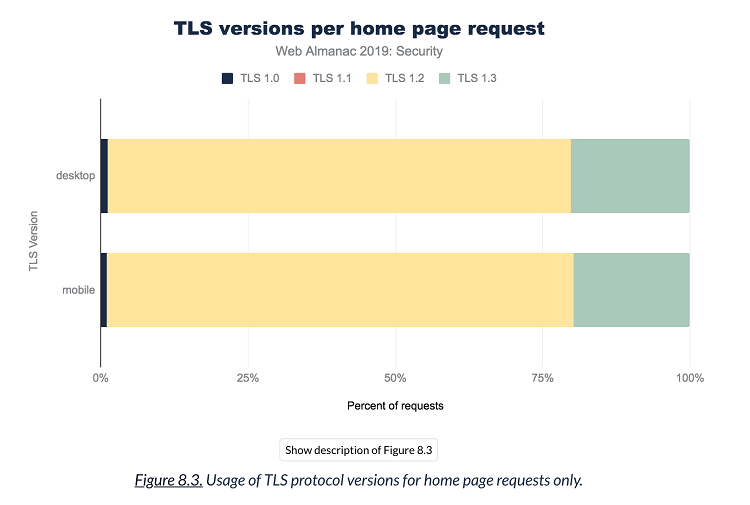
Adoption of the versions of TLS protocol (source HTTP Archive)
Interested in web performance? Also read our article about
our optimizations for a fast and secure HTTPS website
